CPPM Policy Chapter 13: Financial Systems and Controls
This Core Policy and Procedures Manual chapter covers policy, and control and security standards for government financial systems. Requirements for the completion of financial risk and controls reviews, as well as, guidance on risk-based internal controls, and standards for accounting assertions and assessment of computer controls are outlined.
- 13.0 Financial Systems and Controls
13.1 Objectives
- ensure that financial systems are developed and implemented with due regard to generally accepted financial control standards, and are consistent with government business and systems strategic direction
- strive towards integrated financial management to support government decision-making, accountability and transparency as described in the Financial Management Information Systems Vision (PDF) (government access only)
- provide guidance to ministries on financial systems, supporting internal controls and financial risk assessments
13.2 General
Financial systems generate a significant amount of data and information, and are a vital component in managing the delivery of government services and in producing the Province of B.C. Public Accounts.
Roles and Responsibilities
Treasury Board has overall responsibility for government financial management and control in the province (CPPM 2.2.3). On behalf of Treasury Board, the Office of the Comptroller General and Treasury Board Staff, Ministry of Finance prepare and release summary financial information, as well as, detailed information on ministries and agencies that make up the Consolidated Revenue Fund and the Government Reporting Entity.
Ministries are responsible for their financial systems and ensuring compliance with government policy and technology standards. The ministry Executive Financial Officer (EFO) or Chief Financial Officer (CFO) where delegated, has overall responsibility for implementation and operation of a financial system (CPPM 2.3).
The Comptroller General is responsible for policy and direction for financial systems, and communication of standards and guidelines (CPPM 2.2.3 & 2.3).
The Government Chief Information Officer is responsible for working with ministries to develop and set corporate policies, standards, processes, procedures, and guidelines for information management and information technology (IM IT) (CPPM 12).
Provincial Treasury is responsible for banking and financial transaction policies and standards, including approving and coordinating ministry acceptance of electronic payments (CPPM 7.2.8).
Definitions
Financial Information – for the purposes of this chapter, means the transactions or data produced or used in understanding, managing, and reporting on the financial aspects of an activity, and is not limited to accounting data. Financial information is relied on to make decisions of a financial nature.
Financial System – for the purposes of this chapter, means a significant system or process (e.g.: manual, automated, end-to-end, feeder, interfaced, central, including data and software applications) that produces or generates financial information. For example, systems that:
- collect, maintain, process, transmit or report financial transactions;
- support internal and external financial report preparation, such as, cost and revenue information, financial statements, and the Public Accounts;
- assist ministries and central agencies with financial management, control, budgeting and forecasting.
Financial Risk and Controls Review (FRCR) – assesses and documents the adequacy of the designed controls for a new financial system (or a significant modification to an existing financial system or a system having a key financial component) with generally accepted financial control standards to prevent and reduce the risk of loss, error, misuse or fraud and to ensure conformity with accounting assertion criteria. (Refer to 13.4.1 for FRCR guidance).
Payment Card Industry Data Security Assessment (PCI-DSA) – an assessment against the policies and standards established by Provincial Treasury for new or existing financial systems that accept payment cards (Refer to CPPM 7.2.8).
Privacy Impact Assessment – an assessment conducted by a public body to determine if a current or proposed enactment, system, project, program or activity meets or will meet the requirements of the Freedom of Information and Protection of Privacy Act.
Security Threat Risk Assessment (STRA) – an information risk assessment process in a form approved by the Chief Information Security Officer, Information Security Branch (Refer to OCIO IM/IT Standards Manual, 6.11 Standard for Information Security Threat and Risk Assessment (PDF)).
Suite of Corporate Financial Systems – the core financial systems which support many of government’s mission critical financial management business functions comprised of:
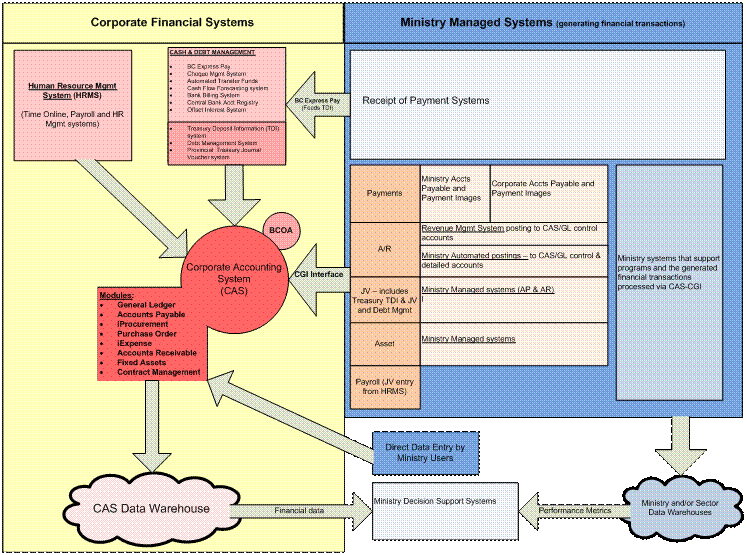
- the financial management and reporting system maintained by CAS, including the general ledger; data warehouse; budget and chart of accounts module; fixed asset module; accounts receivable module; iProcurement, purchase order, iExpenses and accounts payable modules; the corporate contract management module; the CAS Generic Interface; and the common interface for credit card payments.
- the Human Resource Management System, Time On Line and Corporate Human Resource Information and Payroll System maintained by Public Service Agency;
- the banking, cash, debt and investment systems maintained by Provincial Treasury, Ministry of Finance; and
- the revenue and tax collection systems maintained by Revenue Division, Ministry of Finance.
13.3 Policy
- Ministries are responsible for determining the methodology to be used in the development of a financial system. The methodology must be consistent with government architectures for financial systems and information management and information technology (IM IT) policies and standards (Refer to Chapter 12).
- A financial system requires ministry approval prior to placement into production. Ministry EFO approval on the recommendation of the CFO, and Comptroller General acceptance of the FRCR report (Policy 6), is required to implement a new financial system or a significant enhancement to an existing financial system. Financial system documentation needs to support compliance and financial risk and controls assessment.
- Ministries must make use of, to the extent practicable, the suite of corporate financial systems or a component thereof, to process financial information so that core functionality is maximized and not duplicated. In addition, prior to developing any new financial system (or making significant modification to an existing financial system or a system having a key financial component) and/or submitting a funding request for same, ministries must collaborate with OCG1 . This is to ensure that the proposed financial system or enhancement is warranted in addition to what is provided, or is capable of, by the suite of corporate financial systems.
Ministries must receive OCG endorsement before financial system development is substantially initiated or the funding request is advanced further in the budget approval process. The primary point of contact is between the ministry CFO and the Executive Director, Financial Management Branch, OCG. - Ministries must ensure that their financial information processes and financial systems have sufficient and comprehensive controls to prevent and reduce the risk of loss, error, misuse or fraud to an acceptable level. To this end, ministries must complete a pre-implementation FRCR for a new financial system (or a significant modification to an existing financial system or a system having a key financial component). The pre-implementation FRCR must be initiated during system development and completed prior to implementation to production. Ministry resourcing for the FRCR should be identified in the development budget. For FRCR guidance, refer to 13.4.1.
- Qualified, independent and objective parties (internal or external to the ministry) are required to complete the FRCR, at the discretion of the ministry EFO or CFO, where delegated. For example, use of experienced ministry audit or in-house systems staff, such as, a professional accountant (CA, CMA, CGA) with IM/IT audit skills, or a Certified Internal Auditor (CIA) with IM/IT audit skills, or a Certified Information Systems Auditor (CISA) with financial audit skills for the review would be appropriate, as long as the reviewer was not the system developer, operator, or central to the program area that will use the financial system.
In a self-assessment situation, the FRCR should be endorsed by an external service provider or qualified independent ministry staff with the requisite financial and IM/IT audit skills. - The ministry EFO, or CFO where delegated is responsible for approval of the pre-implementation FRCR report. The approved report must be provided to and accepted by the Comptroller General before the ministry implements the financial system to production. The primary point of contact is between the ministry CFO and the Executive Director, Financial Management Branch, OCG. For FRCR report guidance, refer to 13.4.1.
- A post-implementation FRCR must be conducted by the ministry before the third year of operations to confirm that the financial system continues to support business requirements, any weaknesses have been addressed, and key financial controls continue to prevent and reduce the risk of loss, error, misuse or fraud.
Ministry assessment activities and workload for the post-implementation FRCR should be rationalized with those required of any other periodic assessment or assurance engagement (e.g. Reporting on Controls at a Service Organization, Canadian Standard on Assurance Engagements 3416). - The ministry EFO, or CFO where delegated is responsible for approval of the post-implementation FRCR report. The approved report must be provided to and accepted by the Comptroller General before the third operating year of the financial system has commenced. The primary point of contact is between the ministry CFO and the Executive Director, Financial Management Branch, OCG.
- Ministries must ensure that payment transaction systems and processes are developed in compliance with Banking & Cash Management Branch, Provincial Treasury’s policies and standards.
A principal requirement is that people that manage access to, or administer, electronic commerce systems must receive periodic training on how to protect payment card data (refer to the PCI DSS - Resource Centre (government access only) for Security and Awareness Training - government access only), as well as, participate in annual assessments coordinated by Banking & Cash Management against the PCI Data Security Standard. In addition, any new outsourced payment system must be certified as PCI compliant by the EFO prior to deployment.
1Refer to these Guidelines (PDF) (government access only) for additional information on the corporate financial architecture when developing new financial systems to process payments. The guidelines are also intended to support engagement between ministries and OCG.
13.4 Information and References
13.4.1 Financial Risk and Controls Review
Guidance on internal controls, FRCR completion, reporting and approval, and additional control examples are outlined below.
- Risk-based Internal Control
Effective internal controls support achievement of an organization’s objectives. However, a one way or one size approach to designing and managing internal controls is not always realistic given the complexity of various government processes and systems to support them. As an example of the complexity, refer to the Overview of Corporate and Ministry Financial Systems in 13.4.2.
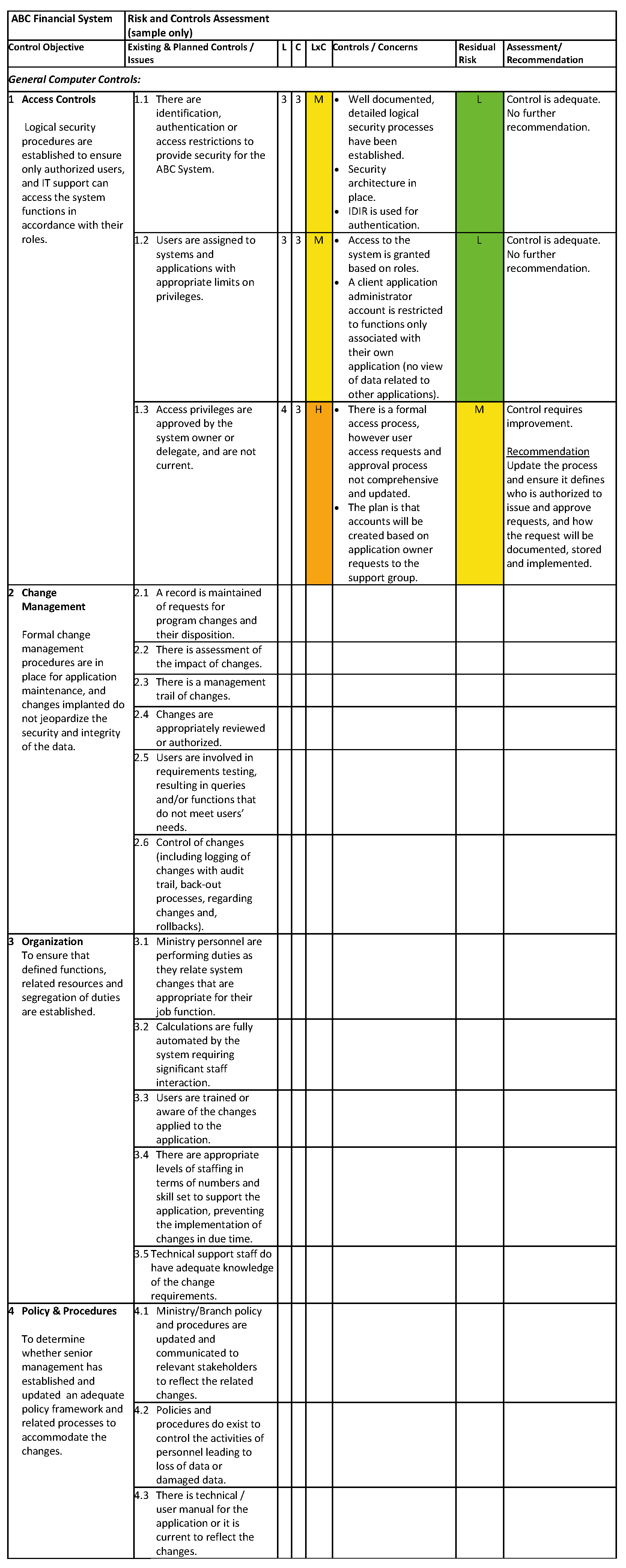
For a financial system, internal controls need to address key risks in the context of the overall business and environment in which it operates. The objective is to ensure an effective internal control regime for financial information and that it is consistent with the standards established for accounting assertions*. For example, assurances that financial transactions are properly authorized, financial records are properly maintained, assets are safeguarded, and that applicable legislation and policies are complied with.
To the extent possible, key controls over financial information and account balances should be automated. It is recognized that automation is not always possible and manual procedures, such as reconciliations and management reviews, may be necessary. It is expected that key automated and compensating controls will form an integral part of user acceptance testing, and their design will be confirmed as part of the FRCR.
* Standards for accounting assertions are as follows:
- Financial information transferred from a ministry financial system to the CAS Financials system, whether detailed or summarized, must meet transaction criteria for:
- Occurrence: recorded transactions actually occurred
- Completeness: all transactions that should be recorded are
- Valuation/Accuracy: correct transaction values are recorded
- Classification: transactions are recorded in the proper account
- Authorization: recorded transactions are valid
- Cut-off: transactions are recorded in the correct accounting period
- For subsidiary ledgers maintained by ministries, the subsidiary financial system balances must meet criteria pertaining to account balances for:
- Existence: asset and liability balances exist
- Completeness: all valid asset and liability balances are recorded and can be reconciled to the CAS Financials system
- Valuation: asset and liability balances are included at correct amount
- Assessment
The FRCR is a formal analysis of a financial system and the environment in which it operates using a risk-based approach. Key risk areas are identified and assessed along with the associated controls established by the internal control regime to mitigate risks. The assessment is supported by a scoping and risk rating exercise to determine whether the financial system includes adequate internal controls.
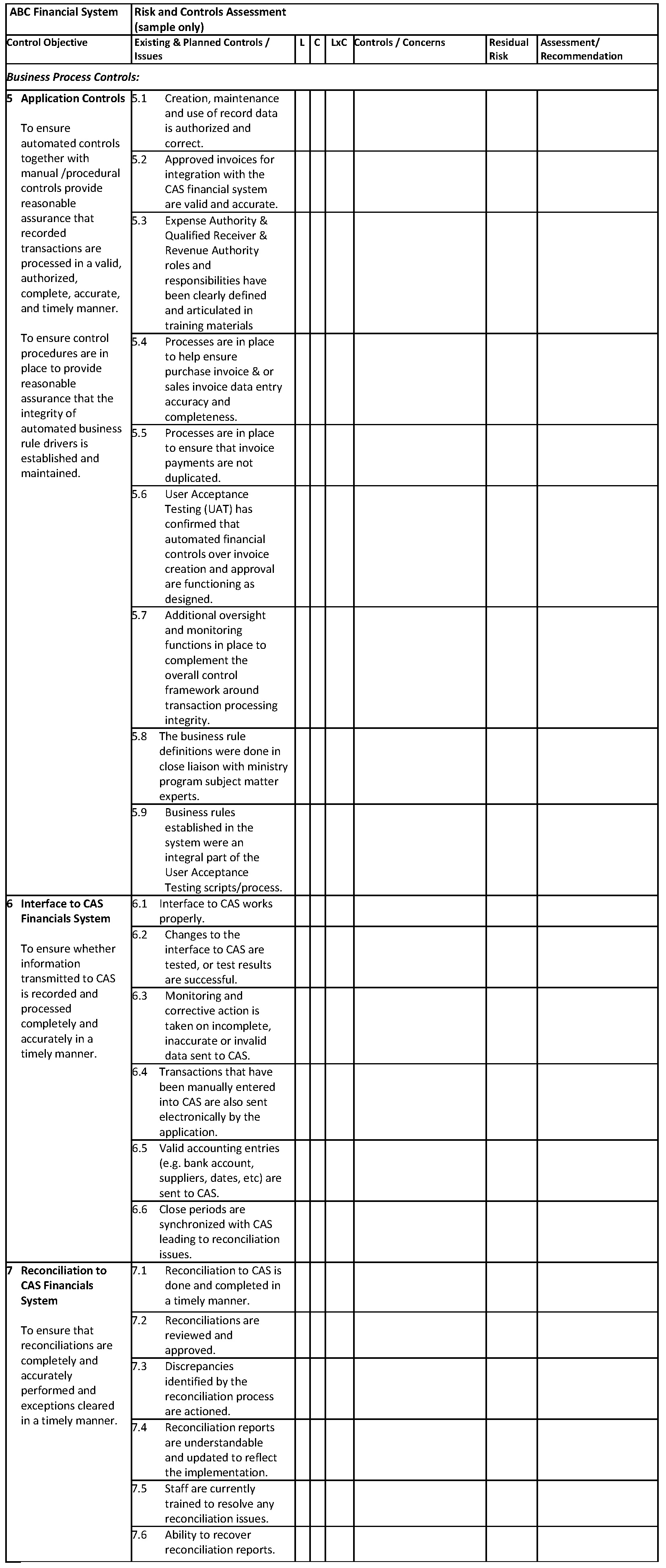
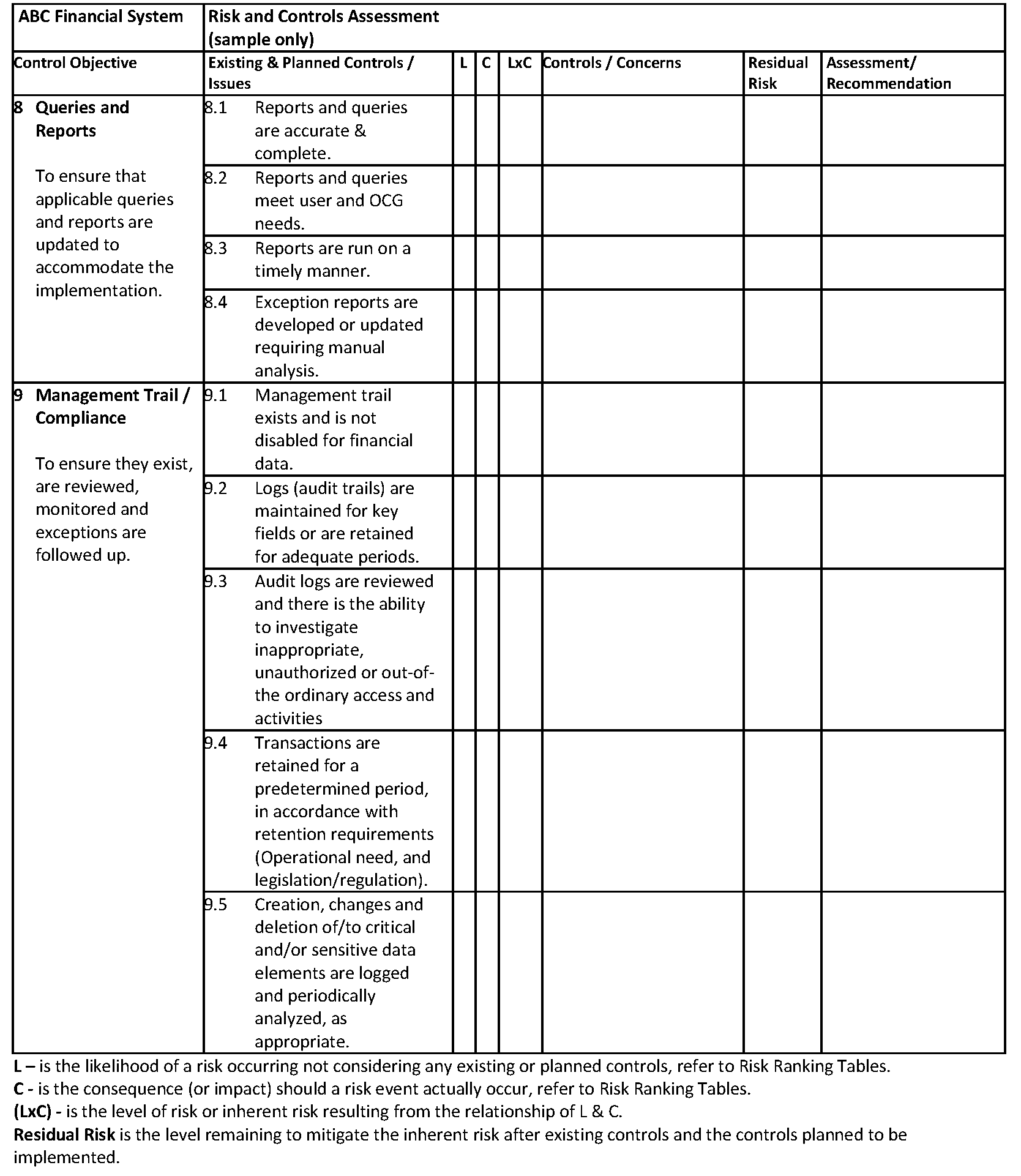
In relation to a financial system the following internal control areas need to be considered:
- Business process controls -- include application controls. The scope of a FRCR needs to address material classes of financial transactions, account balances and summary financial information. Use quantitative and qualitative factors to determine whether or not the application supports material items. For example, review the dollar value of material transactions and the complexity of the accounting policies, or susceptibility of the process to error and fraud to determine the significance of the application/system and control objectives.
When the review of financial transactions/business processes for quantitative and qualitative factors is complete, overall significance and risk can be established. This is then used to determine the in scope financial transactions/business processes which need to be assessed by the FRCR.
- General computer controls – include controls for system development, changes, access to programs and data, and continuity of operations, specifically business continuity, disaster and back-up recovery plans. In addition, the overall governance of the financial system and the definition and assignment of roles and responsibilities, including segregation of duties are considered. Refer to the COBIT2 control framework for detail information.
For the in scope application/system, the general computer controls in place to support the application are identified. When completed a risk assessment for each unique control area can be established. The risk ratings assist in identifying the priority of the general computer controls for the application and the FRCR.
Assessment activities for FRCRs should be coordinated with other assessments required by legislation or policy including a Security Threat and Risk Assessment (STRA), Privacy Impact Assessment, and Payment Card Industry Data Security (PCI-DSA) assessments. The review and assessment activities involve systems or programs with similar operating environment and security concerns and will likely generate common control and risk management information.
2 COBIT (the Control Objectives for Information and related Technology) is a framework or set of best practices for information technology management and has become a common standard for information technology related controls. COBIT provides users with a set of generally accepted measures, indicators, processes and practices to develop appropriate information technology controls. For additional information, refer to the ISACA website.
- Report & Approval
The control objectives, assessed risks, key controls, residual risk, and final assessment comments need to be documented, preferably in matrix form (see the template in 13.4.3) to support the review and remedial of any weaknesses. While generic, completion of the matrix requires consideration of the business context and financial implications in relation to the control objectives and risks.
A ministry self-assessment is acceptable when validated by an external service provider or qualified independent ministry staff with financial and IM/IT audit skills.
Ministry EFO sign off, or CFO where delegated, is required before the FRCR report is submitted to the Comptroller General. The FRCR report will also assist the CFO with ministry representations on financial reporting controls in relation to the Public Accounts.
- Additional Control Examples
- User test and acceptance procedures. The procedures need to be conducted, documented and cover financial functionality testing, control functionality testing, and 3CMB data access and extract for corporate control monitoring purposes.
- Restricted access to financial systems, data and applications to only those staff whose responsibilities require access. Also separation of incompatible functions, for example, custody of assets and access to asset data records.
- Input validation to ensure data entry is authorized, accurate and complete.
- Processing checks to ensure all transactions are processed properly.
- Output reviews to ensure the completeness, accuracy and validity of reported information and the adequacy of audit trails.
- System interfaces that are designed and tested to protect the integrity of data exchange.
- Applications which are periodically monitored and reviewed for control effectiveness.
Note: A qualified list of service providers for use by ministries to conduct or participate in FRCRs can be obtained by contacting IAAS, Ministry of Finance: Email: IAACTION@gov.bc.ca Phone: 778 698-5991.
For financial policy assistance, contact the Financial Management Branch, Office of the Comptroller General, Ministry of Finance: Email: OCGMANUALS@gov.bc.ca.
13.4.2 Overview of Corporate and Ministry Financial Systems
13.4.3 FRCR Matrix
Risk Ranking Tables
LIKELIHOOD (L) = Probability of the risk event actually occurring.
| Level | Descriptor | Approximate probabilities: |
|---|---|---|
| 5 | Certain | 90 – 100% |
| 4 | Likely | 55 – 89% |
| 3 | Possible | 25 – 54% |
| 2 | Unlikely | 5 – 24% |
| 1 | Improbable; Rare | 0 – 4% |
CONSEQUENCE (C)= Degree of severity of the consequence.
| Score | Descriptor | |
|---|---|---|
| 1 | Insignificant | Negligible effects. |
| 2 | Minor | Normal administrative difficulties. |
| 3 | Significant | Delay in accomplishing program or project objectives. |
| 4 | Major | Program or project re-design re-approval and re-do required: fundamental rework before objective can be met. |
| 5 | Catastrophic | Project or program irrevocably finished; objective will not be met. |
LEVEL OF RISK (L x C)
| Likelihood | Consequence | ||||
| 1 | 2 | 3 | 4 | 5 | |
| 5 | LOW | MEDIUM | HIGH | EXTREME | EXTREME |
| 4 | LOW | MEDIUM | HIGH | HIGH | EXTREME |
| 3 | LOW | MEDIUM | MEDIUM | HIGH | HIGH |
| 2 | LOW | LOW | MEDIUM | MEDIUM | MEDIUM |
| 1 | LOW | LOW | LOW | LOW | LOW |
Information Management & IT Management < Previous | Next > Risk Management
Referenced Chapters
Referenced Information
Resources
Contact information
Financial Management Branch